When we run our Dangerzone environments through dev_scripts/env.py, we
use the Podman flag `--userns keep-id`. This option maps the UID in the
host to the *same* UID in the container. This way, the container can
access mounted files from the host.
The reason this works is because the user within the container has UID
1000, and the user in the host *typically* has UID 1000 as well. This
setup can break though if the user outside the host has a different UID.
For instance, the UID of the GitHub actions user that runs our CI
command is 1001.
To fix this, we need to always map the host user UID (whatever that is)
to container UID 1000. We can achieve this with the following mapping:
1000:0:1 # Map container UID 1000 to subordinate UID 0
# (sub UID 0 = owner of the user ns = host user UID)
0:1:1000 # Map container UIDs 0-999 to subordinate UIDs 1-1000
1001:1001:64536 # Map container UIDs 1001-65535 to subordinate UIDs 1001-65535
Refs #228
|
||
|---|---|---|
| .circleci | ||
| .github/workflows | ||
| assets | ||
| container | ||
| dangerzone | ||
| dev_scripts | ||
| install | ||
| share | ||
| tests | ||
| .gitignore | ||
| .grype.yaml | ||
| BUILD.md | ||
| CHANGELOG.md | ||
| INSTALL.md | ||
| LICENSE | ||
| Makefile | ||
| poetry.lock | ||
| pyproject.toml | ||
| README.md | ||
| RELEASE.md | ||
| setup-windows.py | ||
| setup.py | ||
| stdeb.cfg | ||
Dangerzone
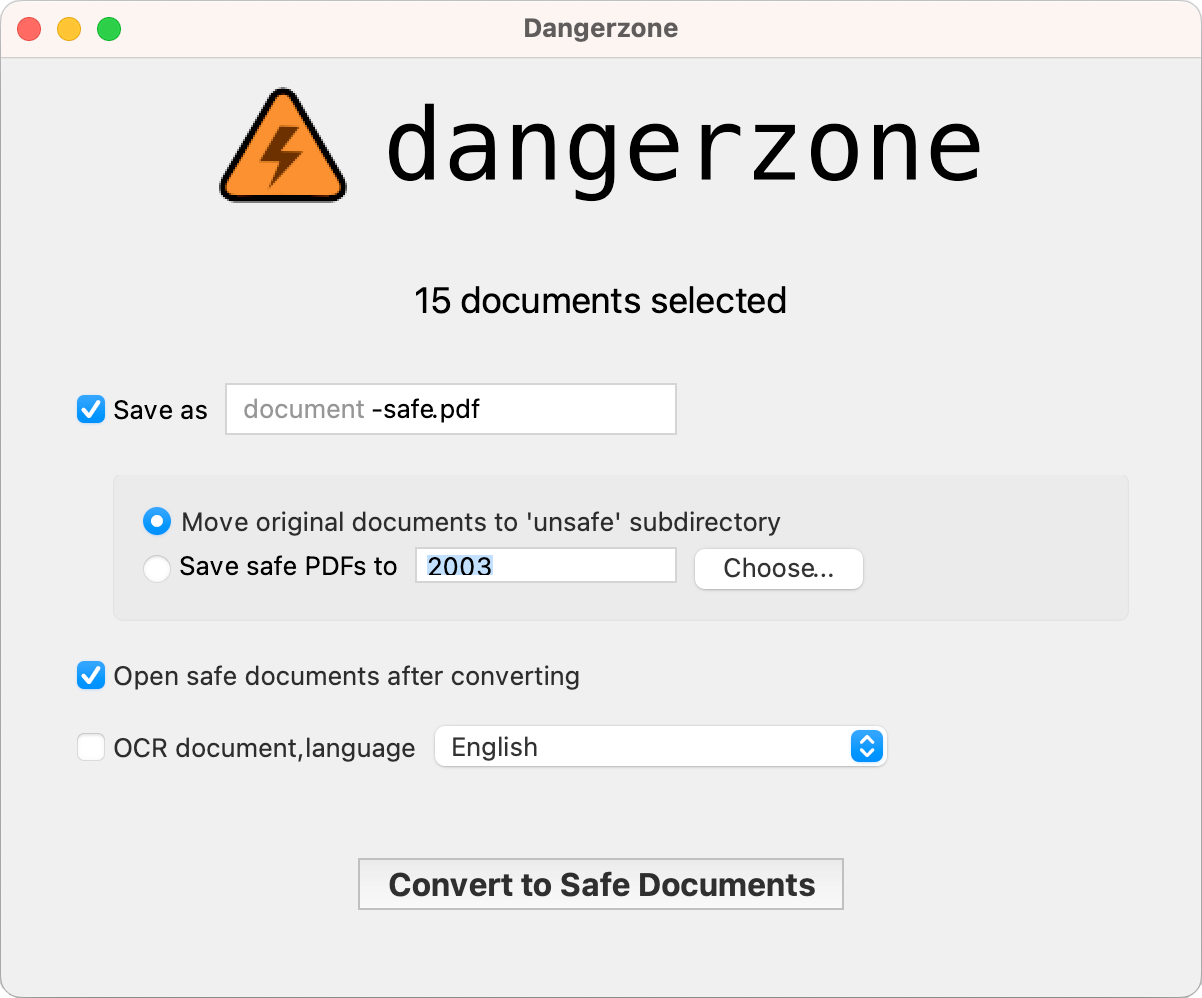
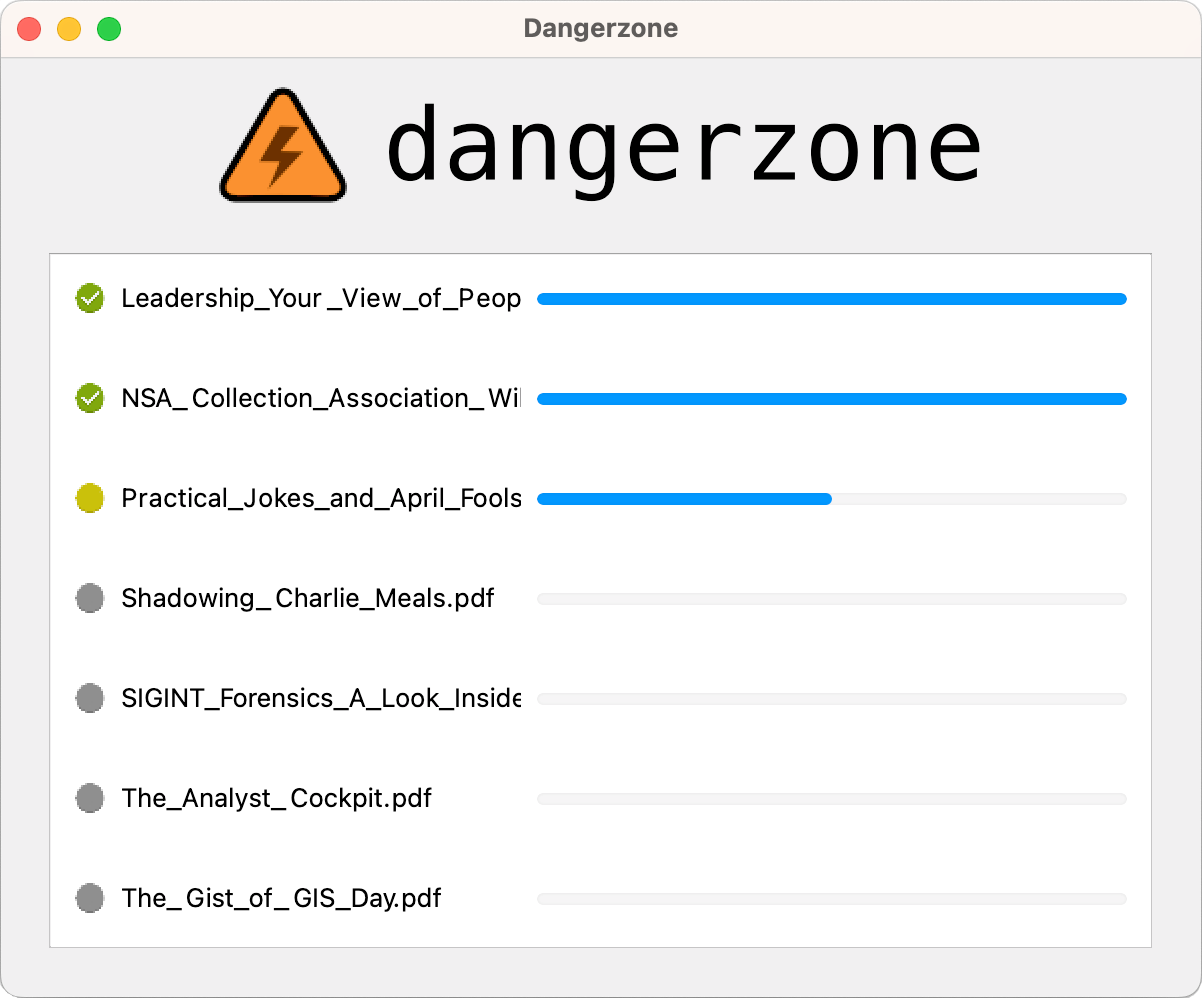
Take potentially dangerous PDFs, office documents, or images and convert them to a safe PDF.
 |
 |
|---|
Dangerzone works like this: You give it a document that you don't know if you can trust (for example, an email attachment). Inside of a sandbox, Dangerzone converts the document to a PDF (if it isn't already one), and then converts the PDF into raw pixel data: a huge list of RGB color values for each page. Then, in a separate sandbox, Dangerzone takes this pixel data and converts it back into a PDF.
Read more about Dangerzone in the official site.
Getting started
- Download Dangerzone 0.4.1 for Mac (Apple Silicon CPU)
- Download Dangerzone 0.4.1 for Mac (Intel CPU)
- Download Dangerzone 0.4.1 for Windows
- See installing Dangerzone for Linux repositories
You can also install Dangerzone for Mac using Homebrew: brew install --cask dangerzone
Some features
- Sandboxes don't have network access, so if a malicious document can compromise one, it can't phone home
- Dangerzone can optionally OCR the safe PDFs it creates, so it will have a text layer again
- Dangerzone compresses the safe PDF to reduce file size
- After converting, Dangerzone lets you open the safe PDF in the PDF viewer of your choice, which allows you to open PDFs and office docs in Dangerzone by default so you never accidentally open a dangerous document
Dangerzone can convert these types of document into safe PDFs:
- PDF (
.pdf) - Microsoft Word (
.docx,.doc) - Microsoft Excel (
.xlsx,.xls) - Microsoft PowerPoint (
.pptx,.ppt) - ODF Text (
.odt) - ODF Spreadsheet (
.ods) - ODF Presentation (
.odp) - ODF Graphics (
.odg) - Jpeg (
.jpg,.jpeg) - GIF (
.gif) - PNG (
.png)
Dangerzone was inspired by Qubes trusted PDF, but it works in non-Qubes operating systems. It uses containers as sandboxes instead of virtual machines (using Docker for macOS, Windows, and Debian/Ubuntu, and podman for Fedora).
Set up a development environment by following these instructions.